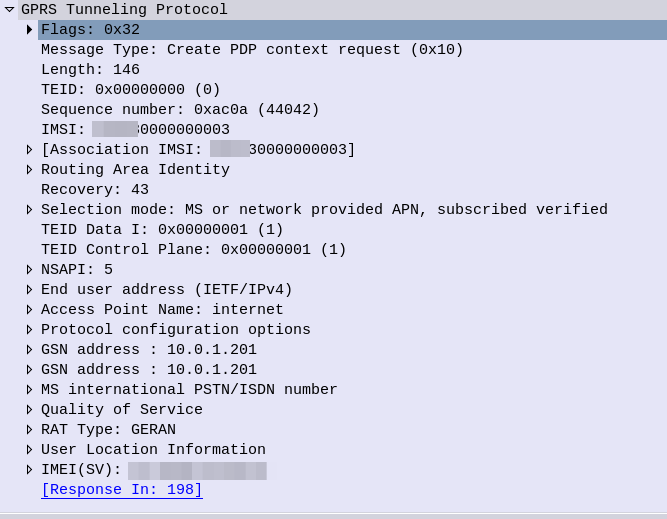
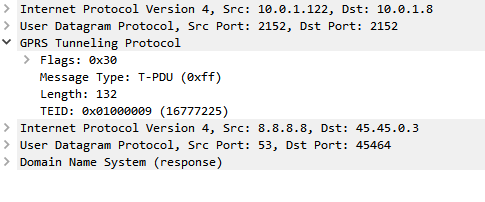
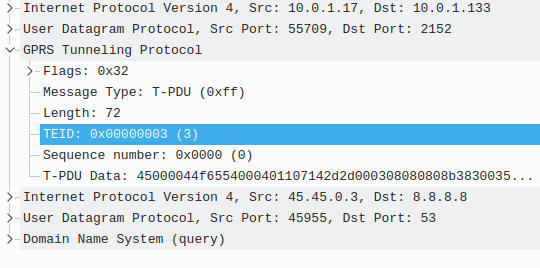
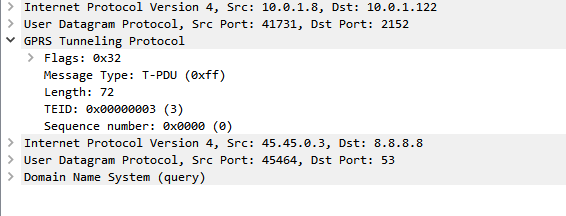
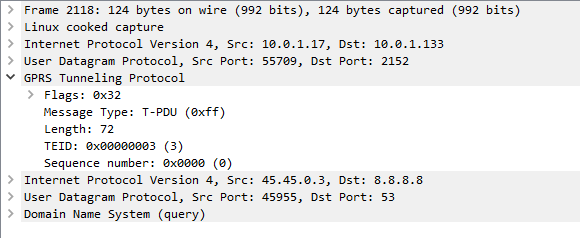
In our last Osmocom post we talked about the basics of packet data, and configuring our BTSs to support it.
In this post we’ll take a look at using Osmocom’s Serving Gateway Support Node (SGSN) named OsmoSGSN.
At the BSC traffic is divided into two categories, Circuit Switched (CS) traffic (Like voice calls & SMS) which is handed by the MSC, and Packet Switched (PS) traffic (Mobile data) is handled by the SGSN.
The SGSN acts as an anchor point for our packet data, it connects our BSC (that handles our RAN) to the GGSN (that handles the connection to external data networks).
Although it’s not technically possible to run a data only 2G/3G network (you require the MSC) it almost could be.
The SGSN handles authentication of subscribers, and runs the PS network completely standalone from the CS network. The SGSN does it’s own handover management, authentication, etc, without any connection to the MSC.
Basic SGSN Config
Like the previous Osmocom network elements we’ve covered, we’ll access the SGSN via Telnet on localhost (the server running the Osmocom stack) on port 4254.
Once we’ve accessed the terminal we’ll escalate our privileges using the enable command, and run configure terminal to start configuring,
We’ll begin by setting the local IP our SGSN will listen on, the gtp local-ip, we’ll need this to be externally accessible for our BTSs, so set it to the IP of the server.
sgsn gtp local-ip 10.0.1.201
Next we’ll need to configure the IP of our GGSN. It gets a bit messy if we’re running everything on one box, as we’re going to have the SGSN and the GGSN trying to communicate on the same ports for GTP, so best to assign an IP in the loopback range, like 127.0.0.2 in my case, for the GGSN:
sgsn gtp local-ip 10.0.1.201 ggsn 0 remote-ip 127.0.0.2 ggsn 0 gtp-version 1 ggsn 0 no echo-interval apn * ggsn 0
We can also steer GGSN selection based on the APN, for example an APN for a corporate network, you may want to have a dedicated GGSN for, for example, we could create a second GGSN – GGSN 1 and route any traffic on our “special.access.net” APN to that GGSN, and everything else to GGSN0:
sgsn gtp local-ip 10.0.1.201 ggsn 0 remote-ip 127.0.0.2 ggsn 0 gtp-version 1 ggsn 0 no echo-interval ggsn 1 remote-ip 10.0.1.99 ggsn 1 gtp-version 1 ggsn 1 no echo-interval apn special.access.net ggsn 1 apn * ggsn 0
You may notice that APNs look like domain names – that’s because they can be,
If we owned the domain special.access.net we could set it to resolve to the GGSN IP we’re using for the special.access.net GGSN at 10.0.1.99, and instead of hardcoding the IP in our config use a DNS server (like 8.8.8.8) to resolve these.
sgsn gtp local-ip 10.0.1.201 ggsn dynamic grx-dns-add 8.8.8.8
But for now, in order to keep our config simple we’ll just configure the one GGSN (GGSN 0) and route all APNs to it:
sgsn gtp local-ip 10.0.1.201 ggsn 0 remote-ip 127.0.0.2 ggsn 0 gtp-version 1 ggsn 0 no echo-interval apn * ggsn 0
Authentication
So the SGSN has it’s own connection to the HSS in order to authenticate subscribers.
Because GSM doesn’t employ Mutual Network Authentication on the SIM we can set the authentication policy on the SGSN to just allow anyone in with any SIM card and they’ll be able to attach and access packet data.
We can easily set this through the VTY:
sgsn
auth-policy accept-all
To enable authentication we’d need to setup the Subscriber in the HLR, like we did for CS only connections, and change the access mode to cs+ps in the HLR.
Then we can change our config to use a remote HLR for authentication,
sgsn
auth-policy remote
A Word on Compression & Encryption
As the demand for traffic on GPRS & EDGE grew, there were still limitations on the bandwidth of the system.
To try and make the best of what’s available, header compression is available, similar to what we’ve seen with ROHC in VoLTE.
To learn more about setting up compression and encryption of the data, take a look in the Osmo-SGSN Manual.
Charging
Charging in mobile networks is a topic we could spend weeks on, but we’re not going to!
OsmoSGSN implements a simple CDR based charging mechanism that writes to a text file a simple CSV file with most importantly the IMSI and bytes in / out for each subscriber, that can be used to implement offline charging (Post paid) if required, and with some hacky scripts can even cut off sessions after reaching a certain amount of throughput (online charging aka pre-paid).
By adding the below to our config OsmoSGSN will write CDRs into /home/nick/sgsn.cdr every 60 seconds.
sgsn cdr filename /home/nick/sgsn.cdr cdr interval 30
The complete Setup
Here’s a complete copy of my running config, you’ll obviously need to change the 10.0.1.201 IP that I’m using to the IP you’re using for your server.
osmo-sgsn.cfg