Samsung handsets have a feature built in to allow debugging from the handset, called Sysdump.
Entering *#9900# from the Dialing Screen will bring up the Sysdump App, from here you can dump logs from the device, and run a variety of debugging procedures.
Samsung share information about this app publicly on their website,
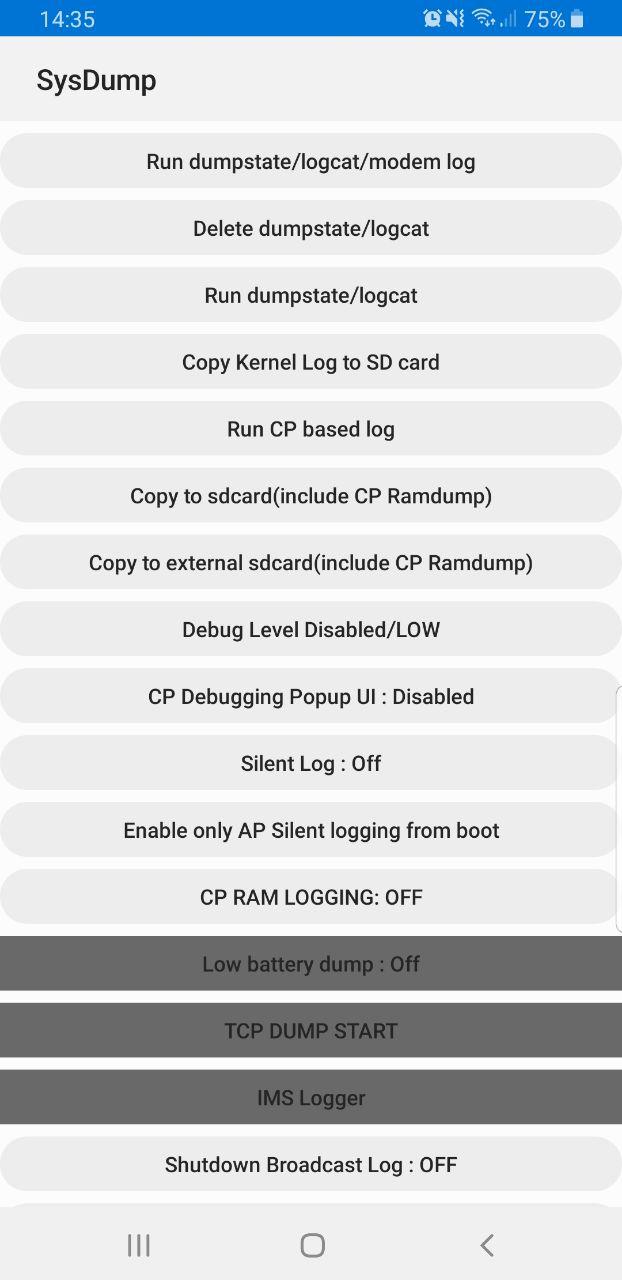
But for private LTE operators, the two most interesting options are by far the TCPDUMP START option and IMS Logger, but both are grayed out.
Tapping on them asks for a one-time password and has a challenge key.
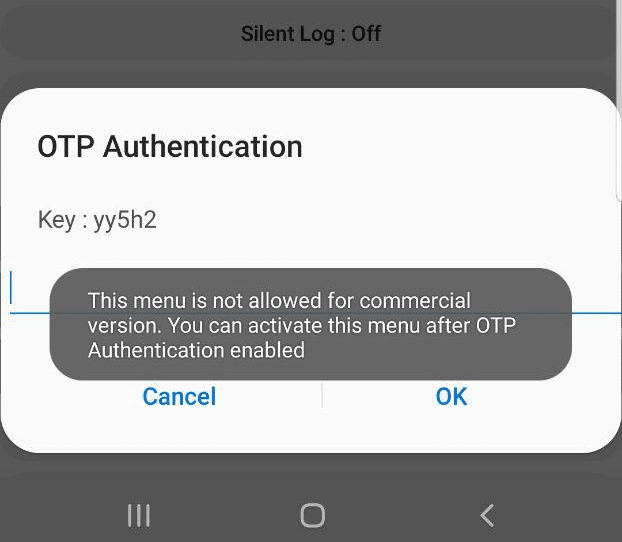
These options are not available in the commercial version of the OS and need to be unlocked with a one time key generated by a tool Samsung for unlocking engineering firmware on handsets.
Luckily this authentication happens client side, which means we can work out the password it’s expecting.

For those who just want to unlock these features you can click here to run the tool that generates the response.
Once you’ve entered the code and successfully unlocked the IMS Debugging tool there’s a few really cool features in the hamburger menu in the top right.
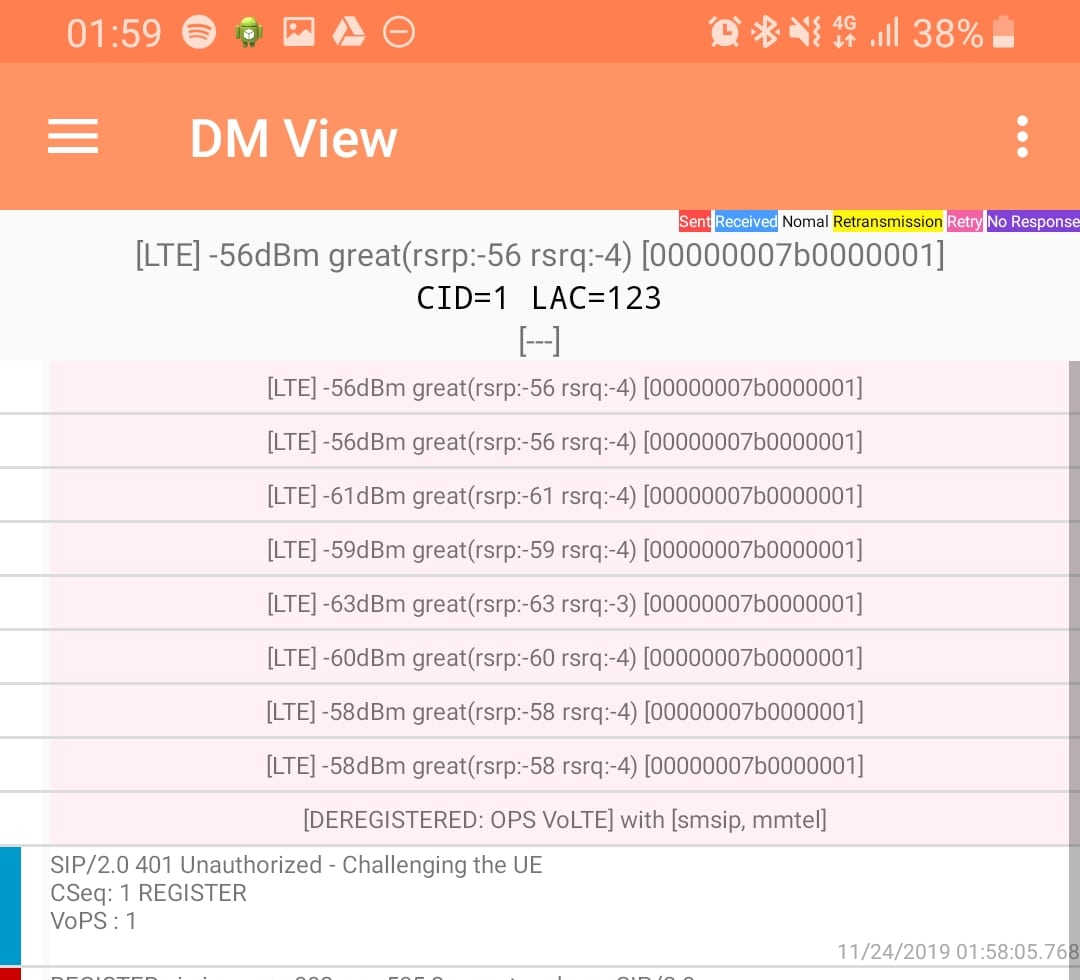
DM View
This shows the SIP / IMS Messaging and the current signal strength parameters (used to determine which RAN type to use (Ie falling back from VoLTE to UMTS / Circuit Switched when the LTE signal strength drops).
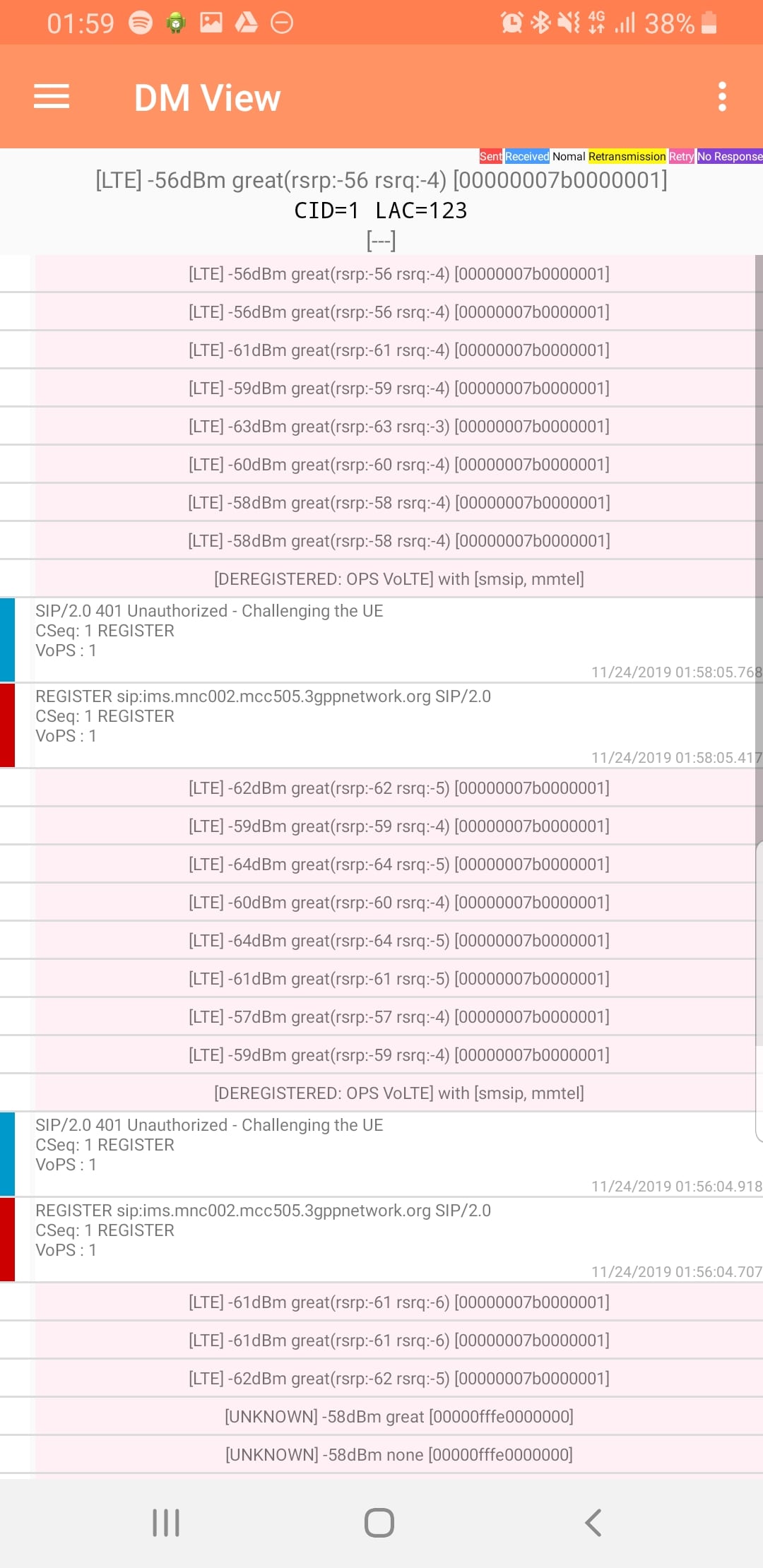
Tapping on the SIP messages expands them and allows you to see the contents of the SIP messages.
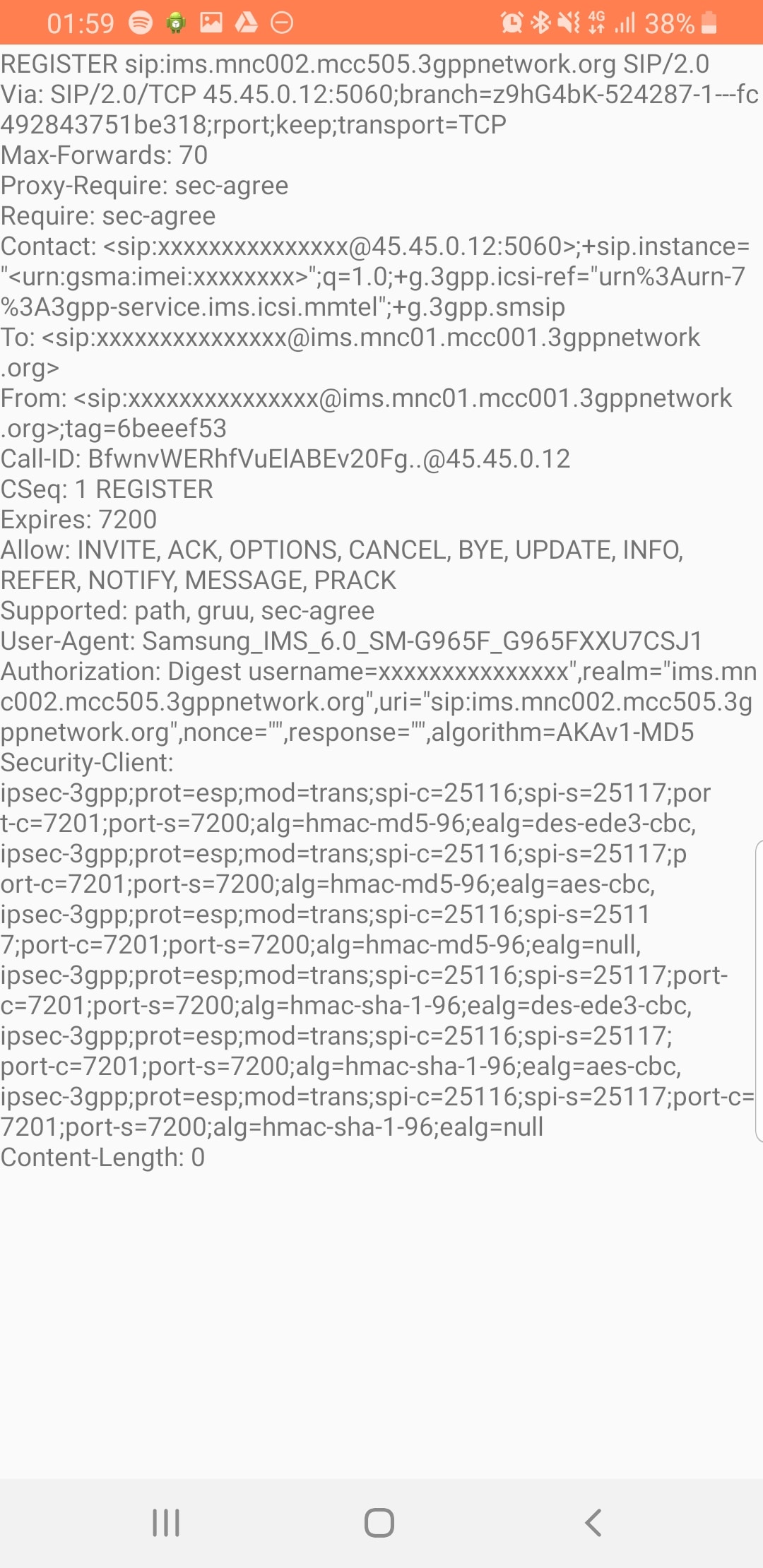
Interesting the actual nitty-gritty parameters in the SIP headers are missing, replaced with X for anything “private” or identifiable.
Luckily all this info can be found in the Pcap.
The DM View is great for getting a quick look at what’s going on, on the mobile device itself, without needing a PC.
Logging
The real power comes in the logging functions,
There’s a lot of logging options, including screen recording, TCPdump (as in Packet Captures) and Syslog logging.
From the hamburger menu we can select the logging parameters we want to change.
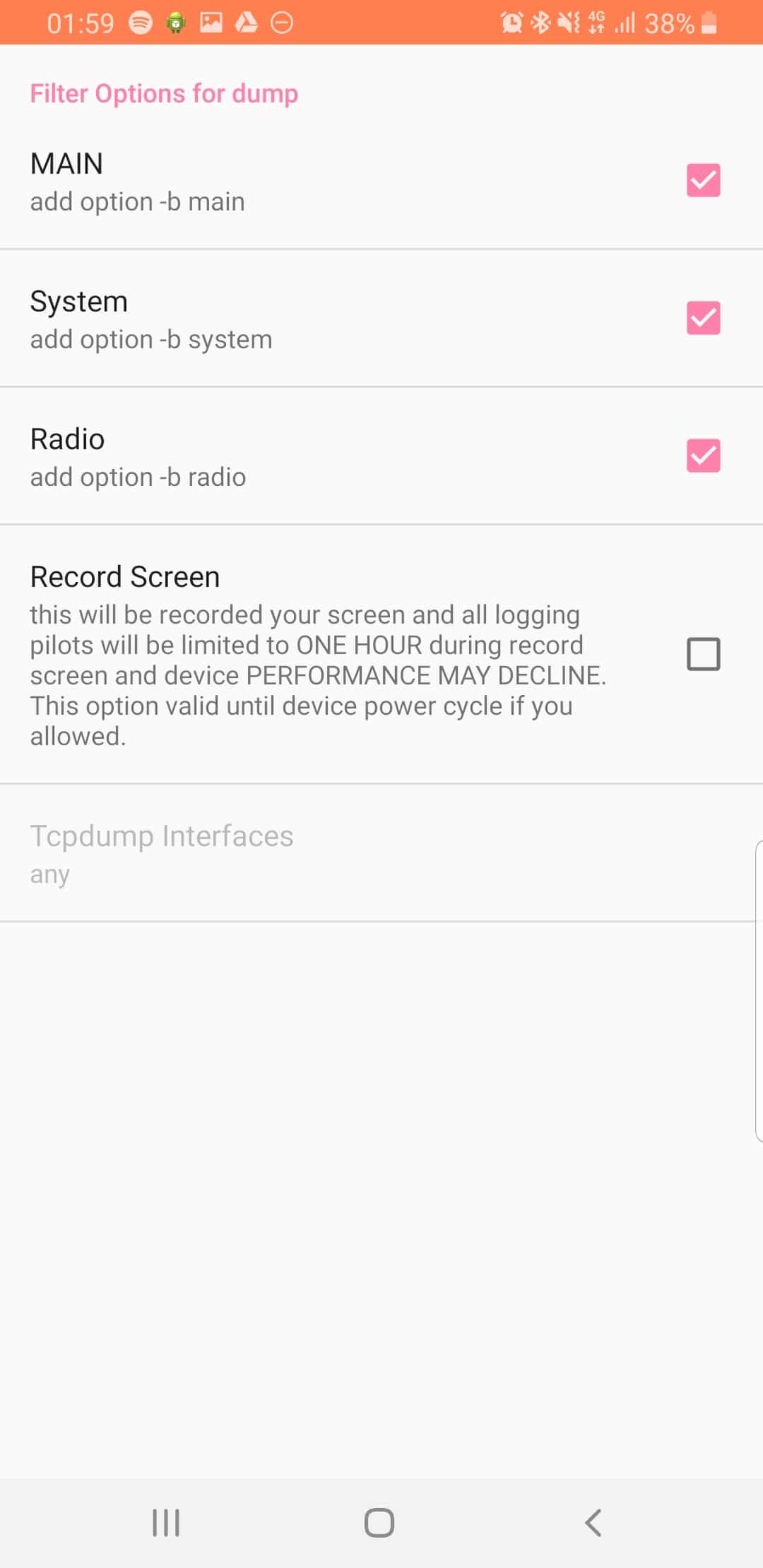
From the Filter Options menu we can set what info we’re going to log,
If you’re leaning about VoLTE & IMS networks, or building your own, I’d suggest checking out my other posts on the topic.
Nick I’ve run into a bit of a problem and I need a suggestion, please.
I’ve unlocked TCP Dump Start, but the IMS Logger has moved to a new location in the IMS settings under *#*#467#*#* (I had to use Google Dialer sadly).
My TCP Dumps are still unlocked but in IMS Logger the DumpMachine options have a password under Meminfo which doesn’t trigger a challenge key, so my IMS DM View logs have some information, but it’s not complete. The reason this is so urgent to me is that I got a bad version of QPST and I noticed it was forwarding some of my info to a GitHub address about my EFS, I’m not sure what info though.
Lately with the information I do get to see on IMS Logger, DM View has started to make me think my SIP ID has been jacked.
I get random cross country 11-digit numbers who apparently I’ve have had calls and messages with in the background but it only shows up in DM. It shows me content length in the messages but I can’t see what’s contained in them or what the file transfer was.
My calls always have a 3rd party added on too. I do not what to reflash my phone to because I will lose access to the USB settings to allow me into the EFS which I can’t pull of again, and I’m trying to figure something separate out.
I just need some suggestions on the IMS DumpMachine option page and how to retrieve it’s password so I can see the entire log.
Please email me if you get a chance, I could really use the advice. Big fan by the way.
Best Regards,
Rick
I am having the smell issue with the password requested but both key. Was there a resolution for this? Using samsung s8
*but not key. (Edit above post) Just a pop up asking for a password.
Please delete the mess of a message above with all the autocorrect and spelling errors. This is the message:
I am having the same issue with clicking the memento log. A pop-up asks for a password, but there is no key. Was there ever a resolution for this?
If so, what is the remedy?
Hi,
I’m trying to reach IMS Settings using a Samsung S21 and I cannot find it anymore. I used it a lot of times with Samsung S5, S6, S8. Do you have any idea how I can launch it ?
Do you know how “TCP dump start” works? I cannot generate any pcap file … (OTP step is ok)
Related to the tools, you can use Shannon DM to see all the messages exchanges by the Samsung phones with Exynos chipset and with the network.
If you have Qualcomm routed phones you can use Network Signal Guru a much better tool , take a lok at my blog: https://volteromania.blogspot.com/p/10.html . You can join the NSG community on Telegram: https://t.me/networksignalguru
cheers
Hi Seth,
I don’t have access to the newer Samsung handsets, it’s possible that Samsung have caught onto this post and secured the system again and only have the option on Engineering Handsets.
Down alliance shield x
And search of ims
You get into the ims settings that way with the s21 ultra
Perfect, it works with alliance shield x. I can access IMS Settings in this way on Samsung S21. Thanks
Yeah possibly not working on later handsets. See https://nvd.nist.gov/vuln/detail/CVE-2019-11341
Nice
my phone does not show the microphone icon on top and also there is no sound when i switchoff and turn on my mobile.
please guide me about this issue
Hello, my Galaxy A51 is not registering in IMS even though I opened another panel of secret IMS settings where it shows “VoLTE Provisioned” and there’s the WiFi calling button on my quick panel that turns dark blue whenever I’m calling with it on.
But somehow there is no VoLTE even though Settings -> About -> SIM Information shows “Mobile voice data type: 4G”
In my mom’s Galaxy Note 10 lite it works as expected.
Both are in OEM ROM. So it should just work. I don’t want to have to call entel (my carrier) if I can help it.
I’m aware I should probably just ditch it and get something newer after almost 6 years (5 in my case because my unit was made in December 2020) and it will probably just work.