Today I was updating a SIM profile for work, the client is rebranding and we need to remove all references to their old brand from the SIM profile.
I’ve written about using Wireshark to view APDU traces on SIM cards before, but today I had a simple need, to find all files with the client’s brand name in them.
I started off just updating the SPN, OPN, etc, etc, but I had a suspicion there were still references.
I confirmed this pretty easily with Wireshark, first I started a trace in Wireshark of the APDUs: I enabled capturing on a USB Interface:
modprobe usbmon
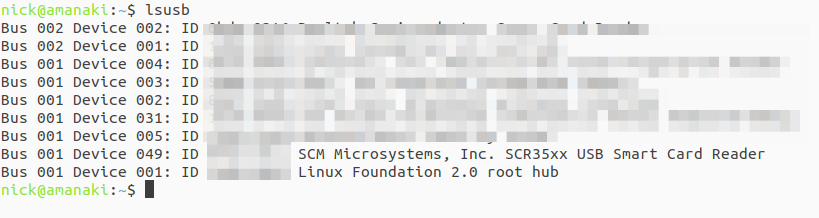
Then we need to find where our card reader is connected, running ‘lsusb‘ lists all the USB devices, and you can see here’s mine on Bus 1, Device 49.
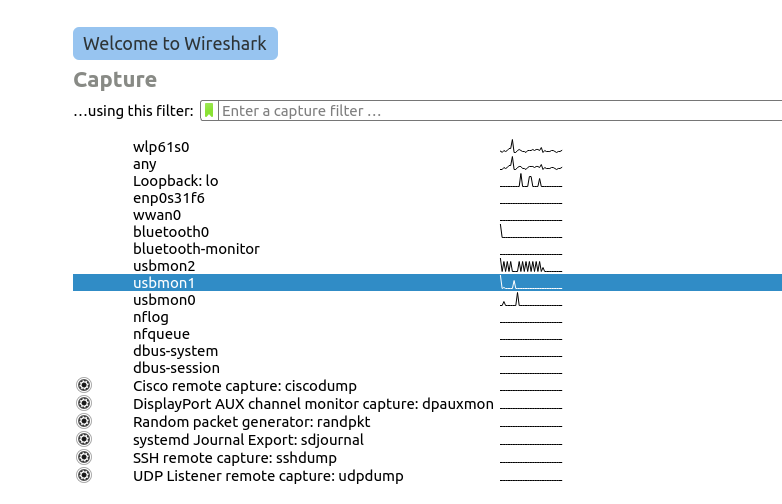
Then fired up Wireshark, selected USB Bus 01 to capture all the USB traffic on the bus.
Then I ran the “export” command in PySIM to read the contents of all the files on the SIM, and jumped back over to Wireshark. (PySIM decodes most files but not all – Whereas this method just looks for the bytes containing the string)
From the search menu in Wireshark I searched the packet bytes for the string containing the old brand name, and found two more EFs I’d missed.
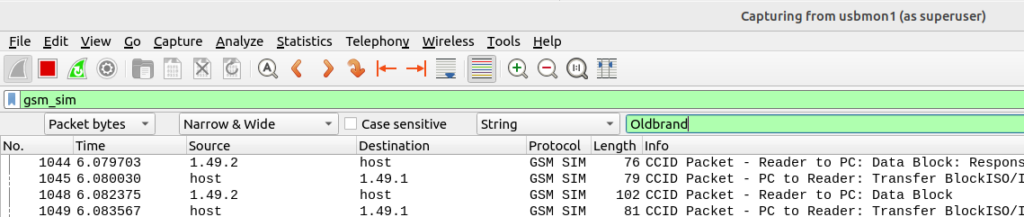
For anyone playing along at home, using this method I found references to the old brand name in SMSP (which contains the network name) and ADN (Which had the customer support number as a contact with the old brand name).
Another great use for Wireshark!
it might be useful to try to write some kind of adapter for this to invoke pySim-trace. The advantage of pySim-trace is that it provides full application-level decode using all the built-in knowledge of pySim, such as keeping track of the currently selected file, decoding the contents while reading/writing in human-readable JSON format, etc.
https://downloads.osmocom.org/docs/pysim/master/html/trace.html
I guess what would be needed is something that parses the CCID packets, strips anything CCID specific so that the raw TPDUs/APDUs remain, and then feed those into the decoders of pySim-trace. The class model is alredy prepared for any number of so called ApduSource implementations, see https://gitea.osmocom.org/sim-card/pysim/src/branch/master/pySim/apdu_source
Thanks Harald, great idea! I know Wireshark has gotten a bit more flexible with it’s decoders and can allow some Python in there, I’ll take a look and see if I can pull in the PySIM stuff!