IPsec ESP can be used in 3 different ways on the Gm interface between the Ue and the P-CSCF:
- Integrity Protection – To prevent tampering
- Ciphering – To prevent inception / eavesdropping
- Integrity Protection & Ciphering
On Wireshark, you’ll see the ESP, but you won’t see the payload contents, just the fact it’s an Encapsulated Security Payload, it’s SPI and Sequence number.
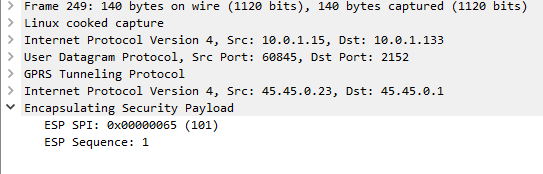
By default, Kamailio’s P-CSCF only acts in Integrity Protection mode, meaning the ESP payloads aren’t actually encrypted, with a few clicks we can get Wireshark to decode this data;
Just open up Wireshark Preferences, expand Protocols and jump to ESP
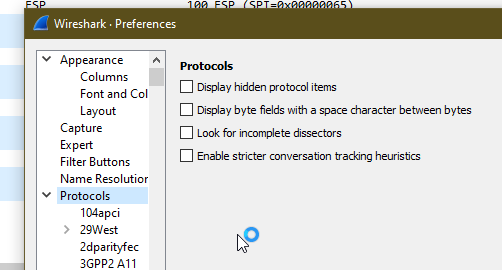
Now we can set the decoding preferences for our ESP payloads,
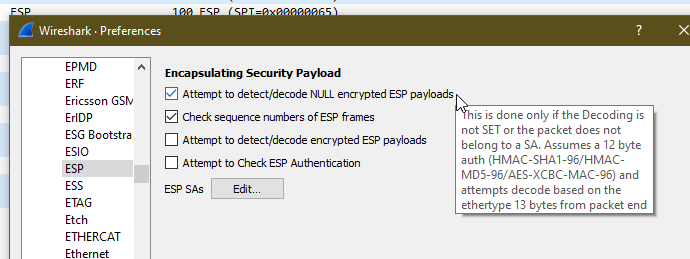
In our case we’ll tick the “Attempt to detect/decode NULL encrypted ESP payloads” box and close the box by clicking OK button.
Now Wireshark will scan through all the frames again, anything that’s an ESP payload it will attempt to parse.
Now if we go back to the ESP payload with SQN 1 I showed a screenshot of earlier, we can see the contents are a TCP SYN.
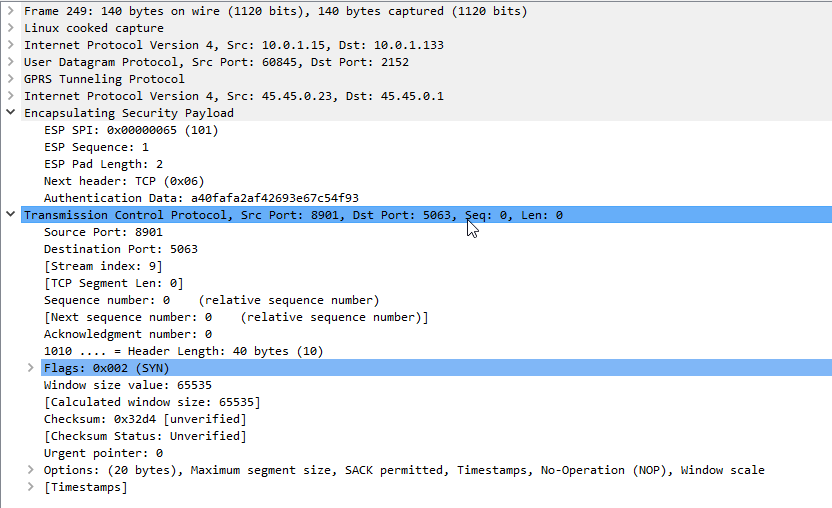
Now we can see what’s going on inside this ESP data between the P-CSCF and the UE!
As a matter of interest if you can see the IK and CK values in the 401 response before they’re stripped you can decode encrypted ESP payloads from Wireshark, from the same Protocol -> ESP section you can load the Ciphering and Integrity keys used in that session to decrypt them.
If you’re leaning about VoLTE & IMS networks, or building your own, I’d suggest checking out my other posts on the topic.
Hi,
What would be the easiest way yo send sip packet to IMS in commercial network. Now I have a rooted A23 Samsung. I want to see if I could send handy crafted invite message to IMS core (instead of phone). By this test I would like to know if the operator is secure if case of chagning the caller id of Callee!