We’ve talked a bit in the Kamailio Bytes series about different modules we can use, but I thought it’d be useful to talk about setting up a SIP Proxy using Kamailio, and what’s involved in routing a message from Host A to Host B.
In the past I’ve talked about the 3 types of SIP proxies out there, stateless, dialog stateful and transaction stateful.
Proxying the initial Request
When we talk about proxying for the most part we’re talking about forwarding, let’s look at the steps involved:
- Our Kamailio instance receives a SIP request (for simplicity we’ll assume an INVITE).
- Kamailio looks at it’s routing logic to lookup where to forward the request to. You could find out where to send the request to from a lot of different sources, you could consult the Dialplan Module or Dispatcher Module, perform an SQL lookup, consult UsrLoc table to find a AoR, etc.
- Add it’s own Via header (more on that later)
- Forward the Request (aka Proxy it) to the destination selected
Let’s take a look at a very simple way we can do this with two lines in Kamailio to forward any requests to 192.168.1.110:
####### Routing Logic ########
/* Main SIP request routing logic
* - processing of any incoming SIP request starts with this route
* - note: this is the same as route { ... } */
request_route {
xlog("Received $rm to $ru - Forwarding");
#Forard to new IP
forward("192.168.1.110");
}
After we restart Kamailio and send a call (INVITE) to it let’s see how it handles it:
192.168.1.75.5060 > 192.168.1.221.5060: SIP: INVITE sip:[email protected]:5060 SIP/2.0 192.168.1.221.5060 > 192.168.1.110.5060: SIP: INVITE sip:[email protected]:5060 SIP/2.0 192.168.1.110.5060 > 192.168.1.221.5060: SIP: SIP/2.0 100 Trying 192.168.1.221.5060 > 192.168.1.75.5060: SIP: SIP/2.0 100 Trying 192.168.1.110.5060 > 192.168.1.221.5060: SIP: SIP/2.0 180 Ringing 192.168.1.221.5060 > 192.168.1.75.5060: SIP: SIP/2.0 180 Ringing
Presto, our request was proxied (forwarded).
Let’s make a small modification, we’ll add a header called “X-Proxied” to the request before we forward it.
####### Routing Logic ########
/* Main SIP request routing logic
* - processing of any incoming SIP request starts with this route
* - note: this is the same as route { ... } */
request_route {
xlog("Received $rm to $ru - Forwarding");
append_hf("X-Proxied: You betcha\r\n");
#Forard to new IP
forward("192.168.1.110");
}
On the wire the packets still come from the requester, to the Proxy (Kamailio) before being forwarded to the forward destination (192.168.1.110):
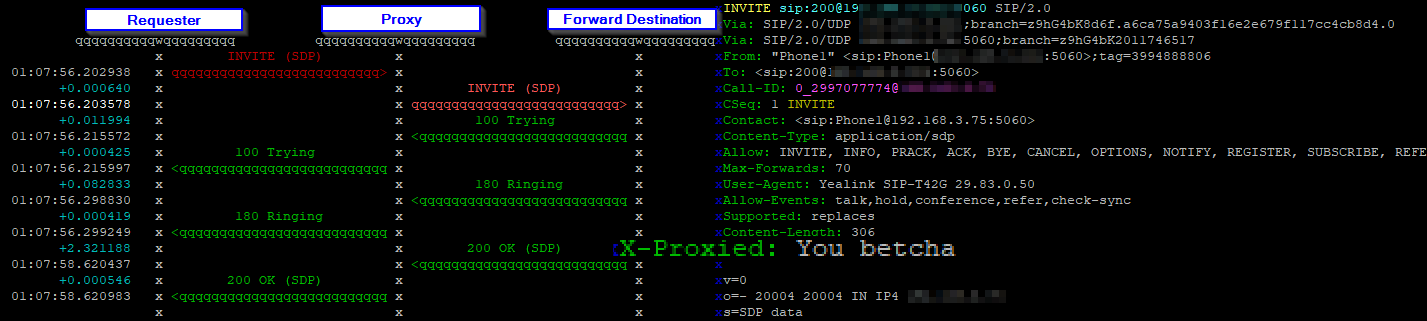
We’ve now got a basic proxy that takes all requests to the proxy address and forwards it to an IP Address.
If you’re very perceptive you might have picked up the fact that the in-dialog responses, like the 100 Trying, the 180 Ringing and the 200 Ok also all went through the proxy, but if you look at syslog you’ll only see the initial request.
/usr/sbin/kamailio: Received INVITE to sip:[email protected]:5060 - Forwarding
So why didn’t we hit that xlog() route and generate a log entry for the replies?
But before we can talk too much about managing replies, let’s talk about Via…
It’s all about the Via
Before we can answer that question let’s take a look at Via headers.
The SIP Via header is added by a proxy when it forwards a SIP message onto another destination,
When a response is sent the reverse is done, each SIP proxy removes their details from the Via header and forwards to the next Via header along.
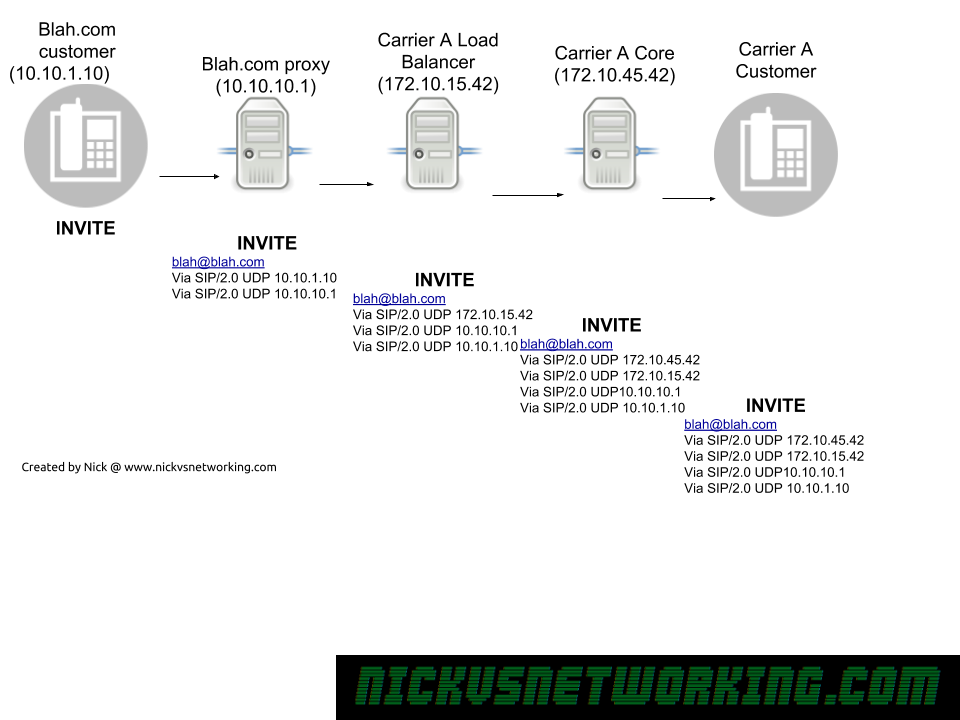
As we can see in the example above, each proxy adds it’s own address as a Via header, before it uses it’s internal logic to work out where to forward it to, and then forward on the INVITE.
Now because all our routing information is stored in Via headers when we need to route a Response back, each proxy doesn’t need to consult it’s internal logic to work out where to route to, but can instead just strip it’s own address out of the Via header, and then forward it to the next Via header IP Address down in the list.
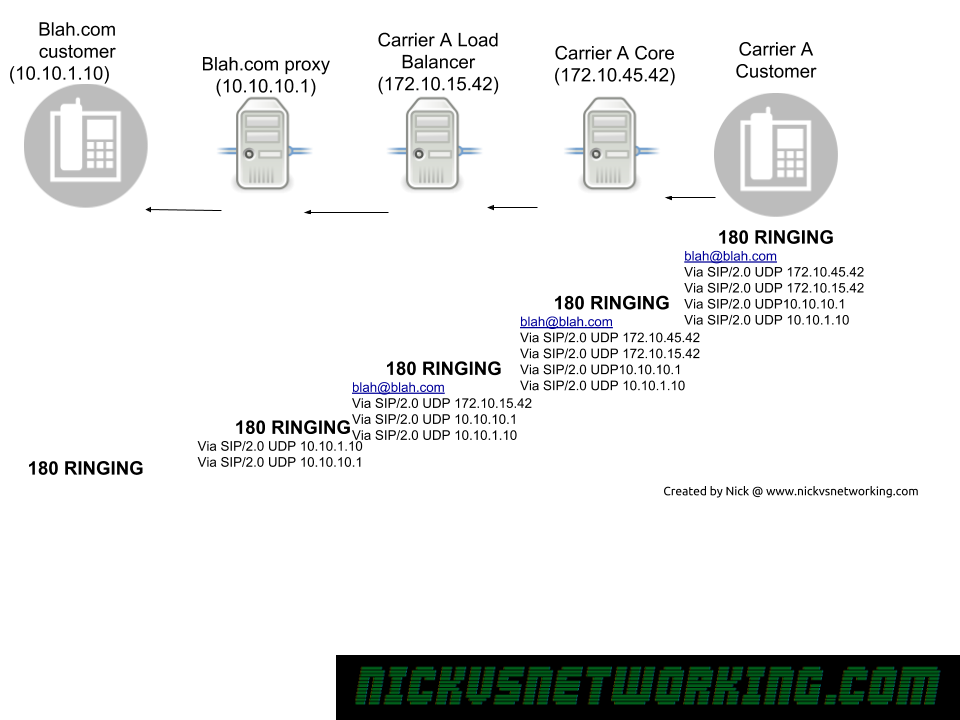
Via headers are also used to detect looping, a proxy can check when it receives a SIP message if it’s own IP address is already in a Via header, if it is, there’s a loop there.
Managing Responses in Kamailio
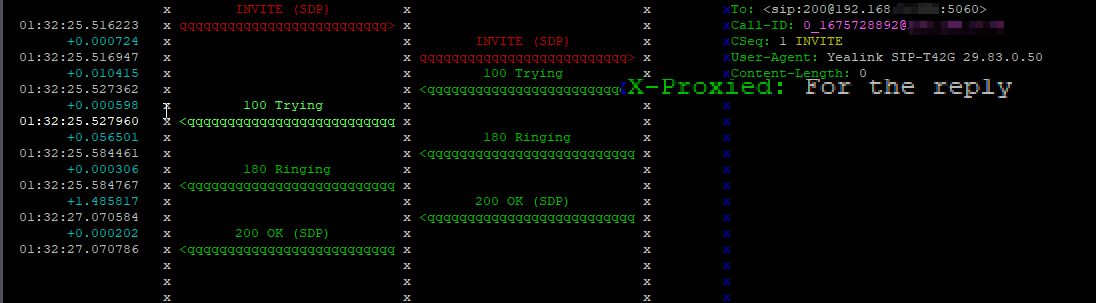
By default Kamailio manages responses by looking at the Via header, if the top Via header is its own IP address, it strips it’s own Via header and forwards it onto the next destination in the Via header.
We can add our own logic into this by adding a new route called onreply_route{}
onreply_route{
xlog("Got a reply $rs");
append_hf("X-Proxied: For the reply\r\n");
}Now we’ll create a log entry with the response code in syslog for each response we receive, and we’ll add a header on the replies too:
Recap
A simple proxy to forward INVITEs is easy to implement in Kamailio, the real tricky question is what’s the logic involved to make the decision,
Very simple solutions but much help in my current case
I used Kamailio for TLS bridging and used forward_udp(IP, 5060);
It make the bridge between TLS and UDP and work like a charm
Thanks so much,
But wouldn’t this stateless proxy just forward traffic in one direction? I was looking at using Kamailio as a SIP proxy for my SIP provider which only supports IP authentication and my FreePBX server is placed in a network with dynamic public ip. So therefore I need to place some kind of proxy at a server which has a static public ip. So I was hoping to use Kamailio for this. But when I look at this configuration it seems like t his only works in one direction – inbound to my “main” SIP server.
How can I expand on this to create a proxy that will act both for inbound and outbound connections? Is that possible? Or is there maybe some other tools/proxies that are better suited for this kind of thing?
I have exactly the same question as Marious Flage does.
Hi Viktor and Marius,
The answer is yes, the proxy will only forward traffic in one direction, unless we use the record-route header which I wrote about in this post.
https://nickvsnetworking.com/sip-concepts-record-routing/
If you put that in then the replies will come via the proxy too.
Hi, is that possible to use kamailio as application server? all i need is to get INVITE, change From field (add display name) and send INVITE back to Requester. the main idea is to get request only once behind the session. for this as i guess, i don’t need kamailio to add via filed with its own ip address and delete its own ip address from route field. is that possible? how can i reach this?