I recently began integrating IMS Authentication functions into PyHSS, and thought I’d share my notes / research into the authentication used by IMS networks & served by a IMS capable HSS.
There’s very little useful info online on AKAv1-MD5 algorithm, but it’s actually fairly simple to understand.
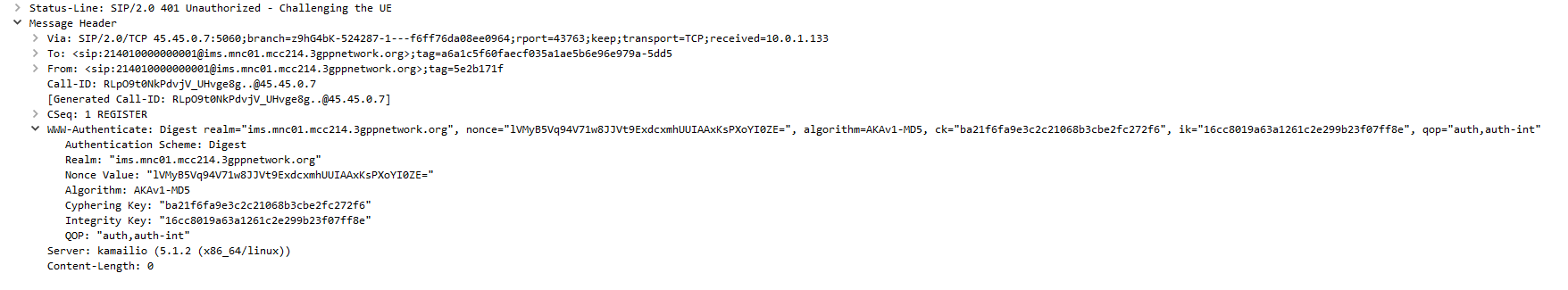
RFC 2617 introduces two authentication methods for HTTP, one is Plain Text and is as it sounds – the password sent over the wire, the other is using Digest scheme authentication. This is the authentication used in standard SIP MD5 auth which I covered ages back in this post.
Authentication and Key Agreement (AKA) is a method for authentication and key distribution in a EUTRAN network. AKA is challenge-response based using symmetric cryptography. AKA runs on the ISIM function of a USIM card.
I’ve covered the AKA process in my post on USIM/HSS authentication.
The Nonce field is the Base64 encoded version of the RAND value and concatenated with the AUTN token from our AKA response. (Often called the Authentication Vectors).
That’s it!
It’s put in the SIP 401 response by the S-CSCF and sent to the UE. (Note, the Cyperhing Key & Integrity Keys are removed by the P-CSCF and used for IPsec SA establishment.
Very nice (small) article Nick!
Thank you for investing time in this.
Nice work. Well Done
Hi Nick, Do you know if the field with Algorithm AKAv1-MD5 is mandatory when request authenticate in SIP Register Message sent by the UE?
I´m asking because I see several 403 Forbidden on some Iphones which are not sending this field on register.
Thanks and regards
Hi Gone, I think it depends on the carrier’s policy because I know some carriers support “MD5”.
Hi Nick!
I’m interested in this topic, but still haven’t found an answer on how the values of “cnonce” and “response” are calculated. Could you by any chance tell me something about them?
Thanks in advance 🙂