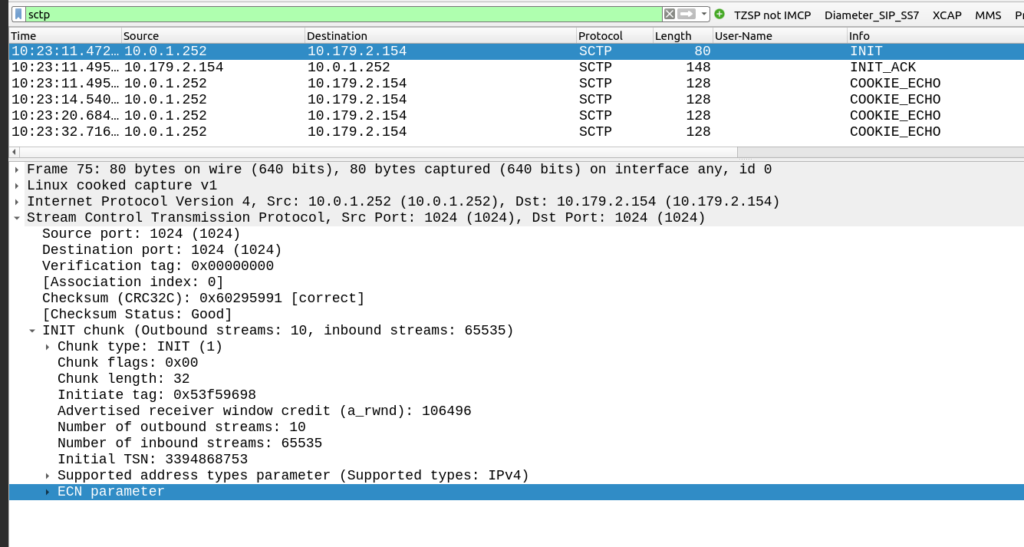
The other side of the SCTP connection didn’t like my SCTP parameters.
My SCTP INIT looked like this:
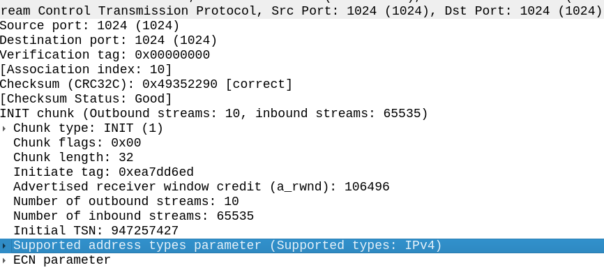
By default, Linux includes support for the ECN and Supported Address Types parameters in the SCTP INIT.
But the other side did not like this, it sent back an ERROR stating that:
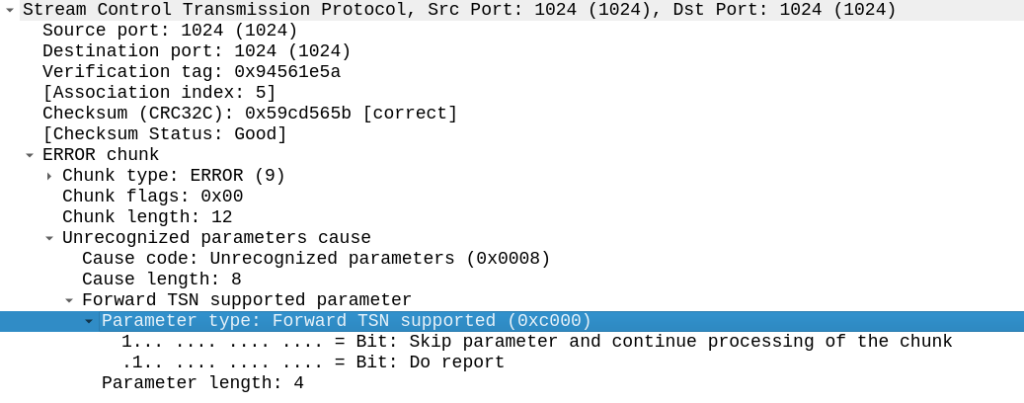
Okay, apparently it doesn’t like the fact that we support Forward Transmission Sequence Numbers – So how to turn it off?
I’m using P1Sec’s PySCTP library to interact with the SCTP stack, and I couldn’t find any referneces to this in the code, but then I rememberd that PySCTP is just a wrapper for libsctp so I should be able to control it from there.
The Manual (of course) has the answers.
Inside /proc/sys/net/sctp we can see all the parameters we can control.
To disable the Forward TSN I need to disable the feature that controls it – Forward Transmission Sequence numbers are introduced in the Partial Reliability Extension (RFC 3758). So it was just a matter of disabling that with:
sysctl -w net.sctp.prsctp_enable=0
And apply with
sysctl -p
And lo, now my SCTP INITs are happy!