While poking around the development and debugging features on Samsung handsets I found the ability to run IMS Debugging directly from the handset.
Alas, the option is only available in the commercial version, it’s just there for carriers, and requires a One Time Password to unlock.
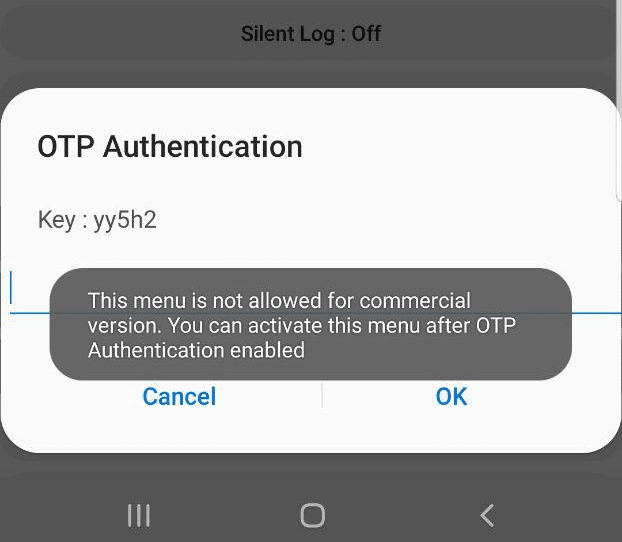
When tapping on the option a challenge is generated with a key.
Interestingly I noticed that the key changes each time and can reject you even in aeroplane mode, suggesting the authentication happens client side.
This left me thinking – If the authentication happens client side, then the App has to know what the valid password for the key shown is…
Some research revealed you can pull APKs off an Android phone, so I downloaded a utility called “APK Extractor” from the Play store, and used it to extract the Samsung Sysdump utility.
So now I was armed with the APK on my local machine, the next step was to see if I could decompile the APK back into source code.
Some Googling found me an online APK decompiler, which I fed the compiled APK file and got back the source code.
I did some poking around inside the source code, and then I found an interesting directory:
Here’s a screenshot of the vanilla code that came out of the app.
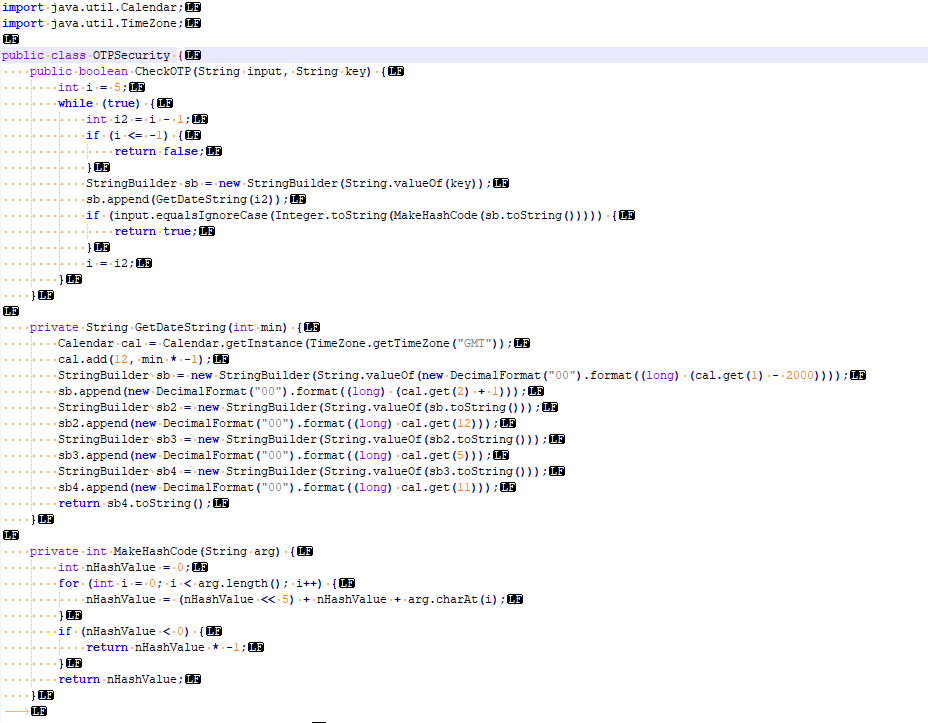
I’m not a Java expert, but even I could see the “CheckOTP” function and understand that that’s what validates the One Time Passwords.
The while loop threw me a little – until I read through the rest of the code; the “key” in the popup box is actually a text string representing the current UNIX timestamp down to the minute level. The correct password is an operation done on the “key”, however the CheckOTP function doesn’t know the challenge key, but has the current time, so generates a challenge key for each timestamp back a few minutes and a few minutes into the future.
I modified the code slightly to allow me to enter the presented “key” and get the correct password back. It’s worth noting you need to act quickly, enter the “key” and enter the response within a minute or so.
In the end I’ve posted the code on an online Java compiler,
Generate OTP Response from Key (Challenge)
Replace yy182 with your challenge. I suggest you try the 0 offset and type it in quickly.
I did a write up on how to use the features this unlocks in this post.
If you’re leaning about VoLTE & IMS networks, or building your own, I’d suggest checking out my other posts on the topic.
hello,
is this stlll working on Android 10?
Yes it just worked on my A10eSamsung Tracfone… I don’t know a ton about any of this madness but I was kind of concerned/intrigued when I noticed that when accessing the *#9900# display that “TCP DropDump” was automatically defaulted to ‘on’. So after digging around I found the link to his java compiler, set the offset to “0” and input the key that it was giving me for OTP and voila, it actually accepted it. Now I just need to figure out how to utilize the options and also find out if the original default to “on” was any sort of security issue that I had. Thanks for help though…
Where can I change the offset to 0?
A list of offsets is generated by the code.
I am generating the OTP on my laptop then enter the code into my Samsung S8. Have never managed to get it to work. So maybe the time discrepancy between the laptop and the S8 is causing the issue
How do I get the code and then type it In the java,I see where the dump is,it gives me.a.code,but if i click back the code is gone and I cant figure out where to type the.code in anyways
the link is dead could you just post the code here or in a gist etc.?
dead link on ejyZKd7l tutorialspoint, could you post it again in online compiler or git gist or comment
Thank you for sharing the java code. I ported it to javascript so it’s easier to run.
https://lart2150.github.io/sam.code.html
This logic can no longer be used on Galaxy s25…
Dont Work on new Samsung Devices 🙁
Heis there a solution for one ui 7 samsung