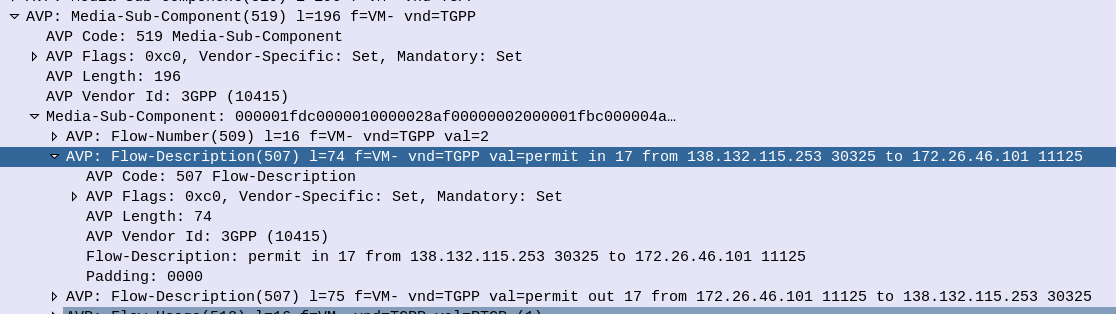
When it comes to setting up dedicated bearers, the Flow-Description AVP is perhaps the most important,
The specially encoded string (IPFilterRule) in the FlowDescription AVP is what our P-GW (Ok, our PCEF) uses to create Traffic Flow Templates to steer certain types of traffic down Dedicated Bearers.
So let’s take a look at how we can lovingly craft an artisanal Flow-Description.
The contents of the AVP are technically not a string, but a IPFilterRule.
IPFilterRules are actually defined in the Diameter Base Protocol (IETF RFC 6733), where we can learn the basics of encoding them,
Which are in turn based loosely off the ipfw utility in BSD.
They take the format:
action dir proto from src to dst
The action is fairly simple, for all our Dedicated Bearer needs, and the Flow-Description AVP, the action is going to be permit. We’re not blocking here.
The direction (dir) in our case is either in or out, from the perspective of the UE.
Next up is the protocol number (proto), as defined by IANA, but chances are you’ll be using 17 (UDP) or 6 (TCP) in most scenarios.
The from value is followed by an IP address with an optional subnet mask in CIDR format, for example from 10.45.0.0/16 would match everything in the 10.45.0.0/16 network.
Following from you can also specify the port you want the rule to apply to, or, a range of ports,
For example to match a single port you could use 10.45.0.0/16 1234 to match anything on port 1234, but we can also specify ranges of ports like 10.45.0.0/16 0 – 4069 or even mix and match lists and single ports, like 10.45.0.0/16 5060, 1000-2000
Protip: using any is the same as 0.0.0.0/0
Like the from, the to is encoded in the same way, with either a single IP, or a subnet, and optional ports specified.
And that’s it!
Keep in mind that Flow-Descriptions are typically sent in pairs as a minimum, as you want to match the traffic into and out of the network (not just one way), but often there can be quite a few sent, in order to match all the possible traffic that needs to be matched that may be across multiple different subnets, etc.
There is an optional Options parameter that allows you to set things like to only apply the rule to open TCP sessions, fragmentation, etc, although I’ve not seen this implemented in the wild.
Example IP filter Rules
permit in 6 from 10.98.254.0/24 5061 to 10.98.0.0/24 5060 permit out 6 from 10.98.254.0/24 5060 to 10.98.0.0/24 5061 permit in 6 from any 80 to 172.16.1.1 80 permit out 6 from 172.16.1.1 80 to any 80 permit in 17 from 10.98.254.0/24 50000-60100 to 10.98.0.0/24 50000-60100 permit out 17 from 10.98.254.0/24 50000-60100 to 10.98.0.0/24 50000-60100 permit in 17 from 10.98.254.0/24 5061, 5064 to 10.98.0.0/24 5061, 5064 permit out 17 from 10.98.254.0/24 5061, 5064 to 10.98.0.0/24 5061, 5064 permit in 17 from 172.16.0.0/16 50000-60100, 5061, 5064 to 172.16.0.0/16 50000-60100, 5061, 5064 permit out 17 from 172.16.0.0/16 50000-60100, 5061, 5064 to 172.16.0.0/16 50000-60100, 5061, 5064
For more info see:
RFC 6773 – Diameter Base Protocol – IP Filter Rule
3GPP TS 29.214 section 5.3.8 Flow-Description AVP
Awesome. Thanks!! I searched thru a host of websites and this had the clearest explanation on flow description.
in example section:
Please remove the spaces between comma separated ports/port ranges.
Just one addition to this exceptional post :
As per 29.214 – Section 5.3.8
NOTE 1: When “ip” as key word is used in the protocol, the port(s) are used to describe the port(s) of any protocol if available.