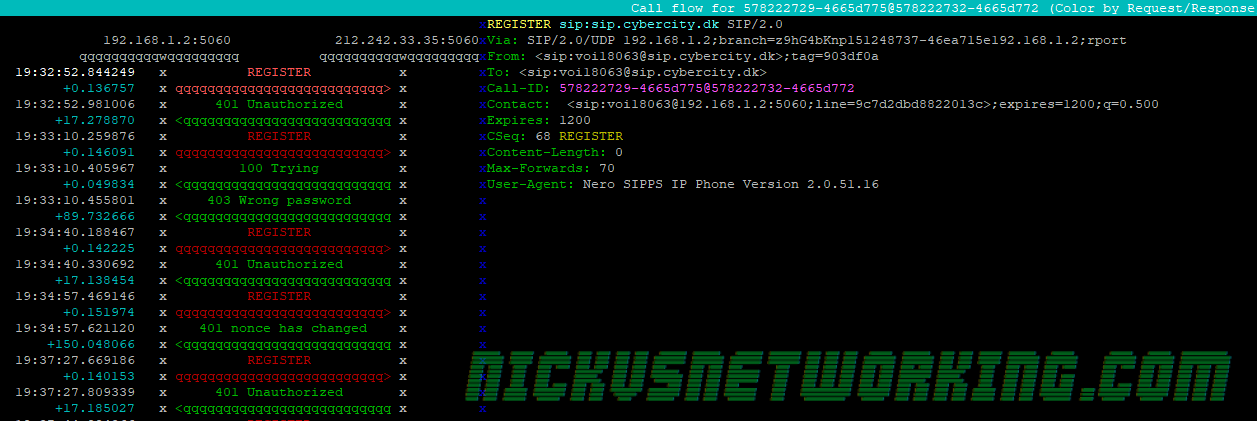
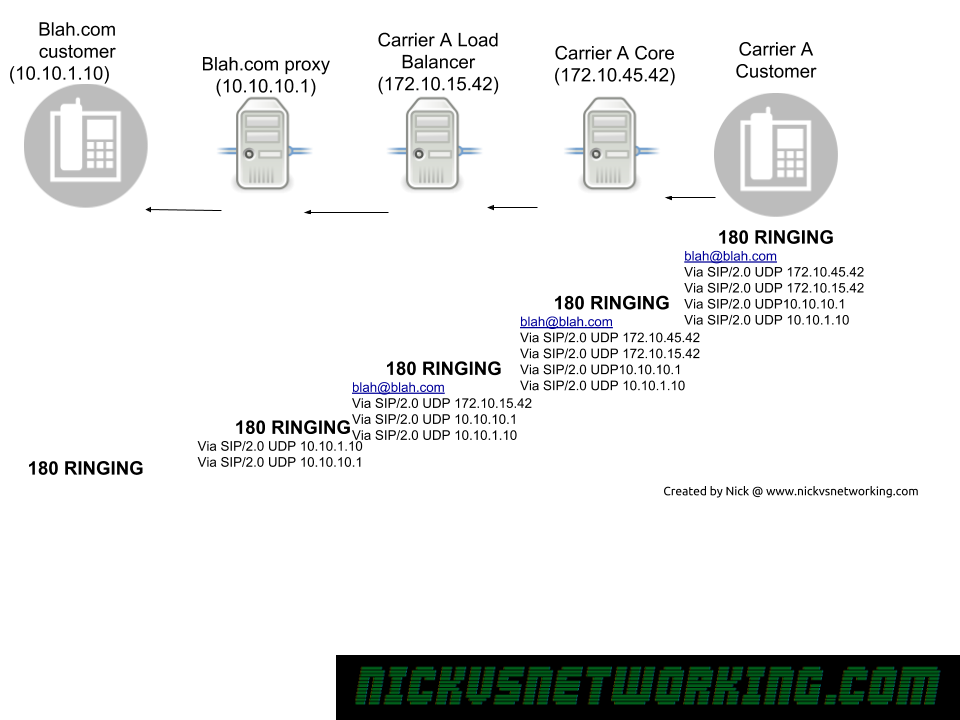
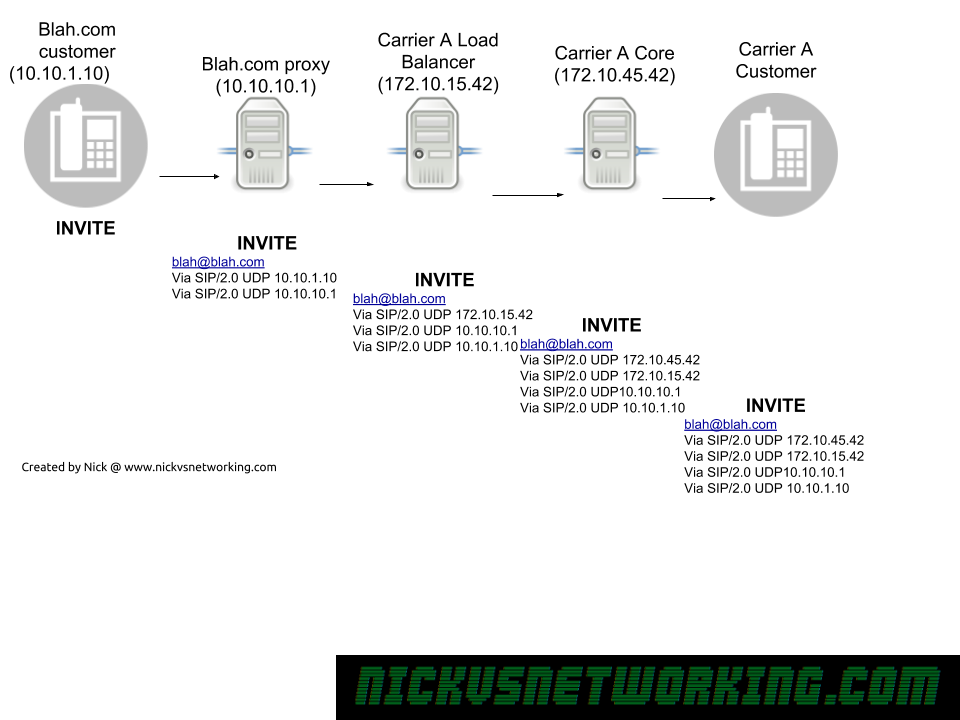
Mostly just reference material for me:
Possible values:
- 0 (ORIGINATING_SESSION)
- 1 TERMINATING_REGISTERED
- 2 (TERMINATING_UNREGISTERED)
- 3 (ORIGINATING_UNREGISTERED
In the past I had my iFCs setup to look for the P-Access-Network-Info header to know if the call was coming from the IMS, but it wasn’t foolproof – Fixed line IMS subs didn’t have this header.
<TriggerPoint>
<ConditionTypeCNF>1</ConditionTypeCNF>
<SPT>
<ConditionNegated>0</ConditionNegated>
<Group>0</Group>
<Method>INVITE</Method>
<Extension></Extension>
</SPT>
<SPT>
<ConditionNegated>0</ConditionNegated>
<Group>1</Group>
<SIPHeader>
<Header>P-Access-Network-Info</Header>
</SIPHeader>
</SPT>
</TriggerPoint>
But now I’m using the Session Cases to know if the call is coming from a registered IMS user:
<!-- SIP INVITE Traffic from Registered Sub-->
<InitialFilterCriteria>
<Priority>30</Priority>
<TriggerPoint>
<ConditionTypeCNF>1</ConditionTypeCNF>
<SPT>
<ConditionNegated>0</ConditionNegated>
<Group>0</Group>
<Method>INVITE</Method>
<Extension></Extension>
</SPT>
<SPT>
<Group>0</Group>
<SessionCase>0</SessionCase>
</SPT>
</TriggerPoint>